Cyber investigators alerted the US Immigration and Customs Enforcement agency (ICE) after a scammer stole $32,000 in cryptocurrency from a 26-year-old cancer patient, Raivo Plavnieks, via a malicious Steam game.
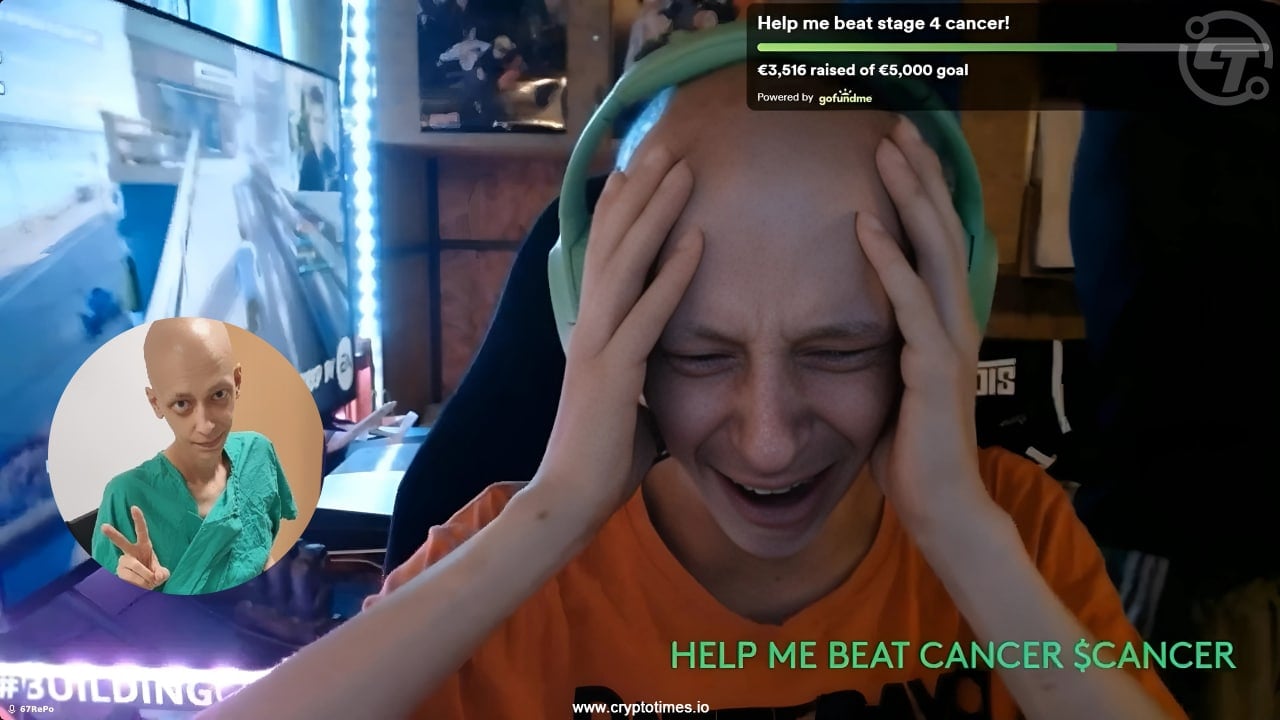
Plavnieks, a streamer battling stage-four sarcoma, had been raising funds for treatment through a Pump Fun token called CANCER, which earned him about $46,000 in rewards.
He was tricked into playing a Steam game called Block Blasters, advertised as providing financial rewards. Instead, it contained malware that drained his cryptocurrency wallet during a livestream.
During the livestream, Plavnieks became visibly upset as the theft unfolded, with a friend attempting to comfort him while they said, “I am broken now.” Support for Plavnieks continues to grow, with his GoFundMe raising nearly €12,000 ($14,000).
More victims affected
The attack impacted more than just Plavnieks. Cybersecurity group VX-Underground analyzed the malicious Steam game. The researcher said it pulled the malware’s infrastructure and victim logs after downloading the suspicious Steam game.
By analyzing hard-coded Telegram credentials and victim logs, researchers documented the campaign’s scale. VX-Underground described the operation as sloppily built, claiming it “took less than 30 minutes” to unravel, and also revealed that more than 900 other victims were affected.
Investigators also noted that one of the attackers’ habits of flaunting their stolen funds online helped identify them, leading to a report to ICE. Steam removed Block Blasters after it was flagged by G Data CyberDefense and reported by multiple users.
Crypto sleuth’s investigation
A collaborative report by VX-Underground, ZachXBT, and other investigators criticized Valve’s handling of Steam’s security. The report described its review system as “deeply flawed,” noting that malware tied to the scam remained online for several weeks.
The report also noted that the attackers pretended to show sympathy and falsely promised to return the stolen funds. Researchers branded Valve’s approach to security as “appalling” and “incompetent,” arguing that such obvious malware should never have been allowed on the platform.
Also Read: UXLINK Token Plunges 99.99% After $45M Phishing Attack